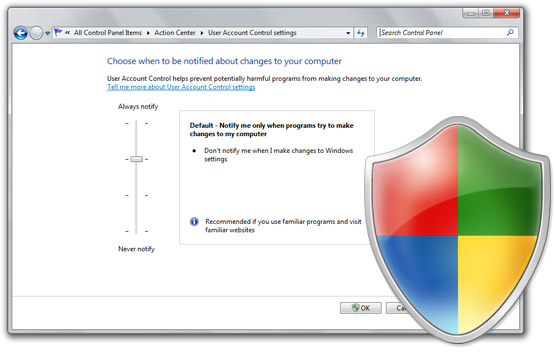
It seemed only hours ago Microsoft stood by their decision not to change the UAC control panel behavior in Windows insisting it was “by design”. Oh wait, it was only hours ago. Nevertheless, three hours and numerous comments later, Microsoft reversed their decision for the better of all Windows 7 users. The Engineering 7 blog writes,
…we are going to deliver two changes to the Release Candidate that we’ll all see. First, the UAC control panel will run in a high integrity process, which requires elevation. That was already in the works before this discussion and doing this prevents all the mechanics around SendKeys and the like from working. Second, changing the level of the UAC will also prompt for confirmation.
The result is actually even slightly better than what I had hoped for. I originally proposed a secure confirmation to be displayed when the UAC level is changed, but Microsoft one-upped that proposal to also run the UAC control panel in high-integrity which means malicious applications cannot manipulate the user-interface of that window without first elevating itself.
All I want to say is thank you to everyone who took the time out to thoroughly understand the issue at hand and continued to spread the message in a constructive and meaningful manner. At the same time I also want to acknowledge everyone who may have disagreed with our opinions for also being constructive.
The day I posted my original article I had lost my ADSL internet connection, and still to this day it is down. So Microsoft, if you disconnected my internet, I’d like to have it back now please. 😛
Update: I’d also like to reiterate, until the RC build of Windows 7 is available, everyone using the Windows 7 Beta should change their UAC setting to “max” to ensure they are safe from either UAC vulnerabilities.
I just got off the phone with Sinofsky, he says that while you may have won the battle, you still can not has internets.
🙂
Huge props to you, Rafael and everyone involved for getting this issue noticed and fixed.
Time to put away the torches and pitchforks! Great news for users and Microsoft alike I think.
Good Stuff Long – great to hear! Bet you’re pretty stoked.
Now if they would only fix that damn line above “games” in the start menu! Drives me crazy! But kudos for them to listening and making the simple changes that were needed to secure the OS. Hopefully there will be less resistance for the next issue, if there is one.
YAY! Great Stuff Long and Rafael!
Woot woot! for Long and Rafael!
Congrats, you just helped Microsoft from a hell of trouble upon their official release 🙂
This story could have ended just like the release of Vista with all the driver issues
I’ve found and proven a third way to bypass the default UAC settings in Win 7 (build 7000). It doesn’t sound like these changes will avoid the problem at all, either, since my method can target *any* process that can perform silent elevation.
My method is more difficult to exploit than the RunDll32 one so it’s not currently important in that regard but what is important is that it may be a lot more difficult to fix. MS could revoke the elevation setting from RunDll32.exe but my method can inject code into any silent-elevation process without requiring elevation itself. Plug the hole in one process and it could simply target another.
I think I’ve shown that the problem needs a much better solution than what’s being proposed so far. (Although, at the same time, the default UAC settings are not useless or anything. They will still stop old attacks and attacks that don’t bother with Win7. My exploit would also be difficult to achieve using a buffer-overflow. So it’s not all bad, but it does mean anything you run on a default Win7 box can get admin access, even if the RunDll32 (etc.) hole is plugged.
Here’s the write-up I just finished, which includes a video demo:
http://www.pretentiousname.com/misc/win7_uac_whitelist2.html
To yourself and Rafael: thank you for your persistence on getting these flaws plugged up. We’ll all appreciate it when Windows 7 hits primetime. 🙂
Very cool. 😀
I dislike Microsoft, I dislike Windows, I dislike Windows 7. I like Linux, I like free software, I like Ubuntu..
But, your efforts are very important!!!
Thanks for all, and I hope a great and fair competition. 🙂
Hey, you are so persistent, and many spanish blogs show this problem thanks to you.
Bye 🙂
PDT: You are “feed”erated.
“Update: I’d also like to reiterate, until the RC build of Windows 7 is available, everyone using the Windows 7 Beta should change their UAC setting to “max” to ensure they are safe from either UAC vulnerabilities.”
I would like to reiterate that even after RTM, everyone should run as standard user and avoid these problems altogether! =)
Signed,
Standard User, and proud of it.
That’s good 🙂
between is it behavior or behaviour, I think I passed your test 😐
Congrats to you and Rafael. Well done!
Well done Long, your persistence paid off! Who says that Microsoft never listens! We will all feel a lot safer now when using Windows 7 thanks to you and Rafael, and I for one am so glad that you kept at it.
From what I can tell, they haven’t actually fixed it. But we’ll see… cautious optimism that this was a simple implimentation flaw and not a incorrect design decision.
The UAC prompt for changing UAC settings is for publicity though.
One time pain of clicking thru those UAC confirmations would be fine but not all the time. Thank for standing for this.
Leo –
“It’s a beta.”
@Brandon: Yes, but if these issues aren’t brought to light now the odds are MIcrosoft won’t do anything about them. Microsoft are terrible at fixing bugs once a product has been released. Do you really want to wait for Windows 7 SP1 for the OS to be as secure as Vista was?
Well done!
Great job now write something good about UAC to mitigate the damage you created
Perfect, good job Long and the community!
1000 Kudos to you, thanks Long. You did an incredible job, making Windows 7 better. Microsoft can be proud to have such support from the community!
This, again, shows that Microsoft always listens to their users’ feedback.
@Lambros Vasiliou – What damage?
So what if a few Mac Fanatics saw it and used it as another “easy” MS bash. No one really cares what fanatics think anyway.
Good job Long. These sort of issues need to be brought to light now and resolved so the non-tech press and non-tech/MacLover blogosphere don’t have another ill-informeed means of slamming a Windows OS.
Great news!
Congrats to you both 🙂 cheers
Thank you Long for all the information and for doing your best to be listened.
Thanks to you, I now know how to keep Win7 beta secure.. because I thought that I was not in danger keeping the settings by default until reading your posts. And it was funny to see discussion on Facebook.
cheers
I, for one, find the whole UAC situation totally overblown.
There is no “the sky is falling” scenario here, unless you are totally inept. Oh wait….most computer users are, so I take it all back. 🙂
Of course with that being said, you can have a sentry of armed guards standing around your computer telling you what to do or not do and it won’t make any difference.
Am I missing something? How does this prevent the second of the two flaws?
http://www.withinwindows.com/2009/02/04/windows-7-auto-elevation-mistake-lets-malware-elevate-freely-easily/
This is a great news! I think all this feedback that Microsoft is receiving from users would help a lot to make Windows 7 even better than it actually is.
Greetings!
good work
I understand why Microsoft changed the UAC after all the whining about Vista. Security over convenience wins one for once.
If I understand correctly, this measure only corrects the possibility that an attacker can disable UAC programmatically, but the same mechanism demostrated in the VB script could still be used to alter silently critical settings like, for example, the built-in Windows firewall, right? If so, this still doesn’t look good enough to me. Correct me if I’m wrong.
It might just be me, but I doubt this site had any influence on the UAC exploit. None-the-less, it did raise awareness of the issue, but still no influence. Sorry.
Long
A big thumbs up to yourself and Rafael for dragging Microsoft kicking and screaming to their senses. In my opinion UAC works perfectly fine in Windows Vista if left alone,
With very little time/effort I was able to extend my previous proof-of-concept code into something that can run any command with elevation and do things like wipe out the OS. This is without using the SendKeys or RunDll32 tricks.
(It took more time to re-do the GUI and make the videos than to turn the “copy a file” concept into “own the machine”. Like I said, if you can copy to System32 and Program Files then it’s game over, as the second of these new videos shows dramatically. Or perhaps over-dramatically. Well, I hadn’t seen the Win7 self-recovery process before so I figured it might be interesting to other people and left it in.)
The first video shows a bit more about how Win7’s COM elevation stuff works:
Mirror 1: http://nudel.kelbv.com/W7E_VID_INT/W7E_VID_INT.htm
Mirror 2: http://leo.lss.com.au/W7E_VID_INT/W7E_VID_INT.htm
The second shows this new code completely hosing a machine without a UAC prompt, in case people don’t realise what “You can open an admin command prompt” means from the first vid. heh:
Mirror 1: http://nudel.kelbv.com/W7E_VID_DRA/W7E_VID_DRA.htm
Mirror 2: http://leo.lss.com.au/W7E_VID_DRA/W7E_VID_DRA.htm
I think that’s as far as I need to take it to make it obvious that something’s not right, one way or another… The prompts provide no security so they should either be removed or secured.
BTW, Cacl.exe and Notepad.exe both have access to create elevated COM objects without prompting. How on earth is that sensible considering that neither process would ever need it? So far it appears that all signed in-box MS executables have the special access. Why make the attack surface larger than it has to be?
For everyone essentially saying “relax, it’s a beta” to continued observations of security leaks – what can I say… Yep, it’s a beta – and thanks to the fine efforts here, it seems the obvious loopholes in the UAC control panel access are being fixed in RC 1.
But that should say something… “RC 1”. A release candidate is supposed to be very close to RTM / FCS / GA and whatever other acronyms you’d like to compare with “final public release”, and this UAC thing is only [i]just[/i] getting some attention in the RC…
Leo’s latest observations seem to make for an even wider “hole” and as he said, has the makings to be much more difficult to plug as well. If a relatively easy to fix UAC control panel issue didn’t get any acknowledgement in the face of so much feedback until RC, you really think MS will run and leap to throw resources, time and effort into a more complex problem “post-RC”? Especially in light of the “problem” seeming to be wrapped up in an implementation they settled on ‘intentionally’ to address usability issues folks complained about in Vista…
I wonder if many of the ppl suggesting to sit back and relax because it’s a beta just don’t think these things are issues, or they agree it’s a problem and think it’ll all just work out WITHOUT the sort of feedback that’s happened here and elsewhere. Or will they also say “relax, it’s only a release candidate” when these issues are left un-addressed – LOL. or MAYBE some of them are hackers who are twisting their moustaches at the prospect of an easy exploit :-)… HA!
But that’s just a curiosity… it’s much more important to find out what Microsoft’s response is to these issues?
@Long/Rafael/Leo… have any of you heard a peep from someone at Microsoft regarding the remaining silent elevation loop hole (Leo – this is the debug process code injection you had found earlier right)?
I’d have to say, like my previous comment, that this is what MS should have responsibly done. At least they are listening to us much more than during the XP years. But can i make a general suggestion to all tech bloggers. Can we please tone down the faux outrage that has been prevalent since the beta was made public (I’ve been using since 6801). Now that this has been addressed. I’ven noticed over the blogisphere that alot of people have now been trying to nitpick issues and hyperbole minor issues, and as such the rage has turned back to the multiple SKU editions (ZOMGWTFBBQ 7 SKU CHOICES NO NOT CHOICE. WHY CANT YOU MAKE IT EASY LIKE APPLE AND GIVE ME NO CHOICE) I do agree that multiple SKU’s are annoying. But when you have a billion customers with unique needs vs 10% of the market users, you have to cater to these different markets.
Lets turn our focus to nudge MS to do things that would change our computing experience for the better. Positive criticism like, Give me true WinFS! Get Rid of the Registry! Move to True EFI.
We’ve shown that MS listens, now lets give them the right message.
Long after one victory?? Maybe you can get MS to fix another issue they have created with the current implementation of UAC in windows 7. I know they are pushing to get 7 out ASAP however fixing the below issue should improve UAC and windows security in the long run; atleast that is what I and others think.
Goto
http://www.pretentiousname.com/misc/win7_uac_whitelist2.html
Now see if you can muster enough outrage for MS to do something about this too.
thank you..
Cool post; I must admit I’m still new to all of this and am trying to get my head around it all but it all seems exciting nonetheless.
To turn off UAC, move the slider to the Off position, and then click OK.
^^::.THE ONLY INFO I EVER REQUIRE.::^^
Hey Long, according to stimator.com, your site is worth an estimated 22,246.00 US Dollars, or 17,621.00 Euros.
Actually… now I don’t care about Windows 7. Completely banning it:
http://tech.slashdot.org/article.pl?sid=09/02/16/2259257
DRM at the max, no thanks.
Forgot to mention..
Making applications by-pass the firewall… isn’t like… you know a security hole?
@Good_Bytes:
That Slashdot article is unmitigated bullshit. Read the comments which rip it apart quite well. It’s the same confused and/or made-up garbage/FUD people spread about DRM in Vista mixed in with some other nonsense.
This comment summed it up well:
http://tech.slashdot.org/comments.pl?sid=1130241&cid=26881973
I can’t believe Slashdot posted that poorly-researched, completely-wrong garbage to their front page and yet didn’t post any of the UAC articles I submitted to them. I guess it matters more who you are rather than what you say on that site. :-/
Agreed. After further research. I was missed-informed. I will be more careful next time, and see other more legit sources before saying a judgment.
My apologies.
This site doesn’t get updated enough – the last post was 6th of Feb. It used to be updated all the time what happened!
I don’t understand how this fixes the problem… Doesn’t this only prevent a program from changing the UAC settings? Who needs to do that if you can auto-elevate, and bypass UAC completely?
Please don’t take this as flame-bait, or excessive criticism of UAC. I just haven’t read anywhere of a really good argument for using UAC that contradicts my experience. I feel like I’m missing a piece of the pie.
I’ve spent most of my career in enterprise environments (thousands of PC’s, hundreds of servers), and have supported a small-business equivalent of home users (family and friends, about 30 machines in all). In the enterprise, workstations are locked down, users have limited access, and all installations are managed via SMS or manual installs performed by a small group with administrative rights, so UAC isn’t really useful (or is there an enterprise model where it is?).
I see the potential benefit of UAC for the home user, although my experience is that home users eventually get tired of the prompts, and ask to have it disabled. Also, making home users reduced accounts can be done, but I find it actually costs more in support effort (because then they HAVE to call me for advanced config, or I have to give them an admin account, which they end up using all the time anyway), and isn’t the purpose of UAC to reduce support needs by reducing infections, etc?
I guess I’m just missing the model where UAC is truly beneficial and it’s objectives can’t be accomplished through other, more traditional methods which are also required for disaster recovery/new systems anyway (real physical firewall, good regular backups, images or unattended setup) .
Any thoughts? What am I missing?
@Jim West: What you are missing is the effect on the windows ecosystem. The reason UAC is so annoying is because most programs want to run with administrator rights when they don’t really need it. Over time, more and more programs will run without UAC prompts (so far there are a lot of programs that used to require admin that don’t anymore).
I agree with JIm West post.
Not only at home, but I think it would be worse at work. At work, people would be more inclined to click OK for anything because “Hey” it’s not your PC or business. Let the supervisor sort it out if anything goes wrong.
Also, mostly no one knows whether they are suppose to click OK to something or not. Why not do an ‘in the wild’ survey of a firm with 100 – 500 employees. Load something they are NOT suppose to elevate or click OK and see how many do.
So, what’s the point of UAC? Except to very knowledgeable geeks!
Don’t expect a firms employees to give a shit about UAC – or even know what it is.
@Andres
Good point-I feel guilty for overlooking that aspect (that some of the incessant UAC prompts come from poorly-designed apps requiring admin rights when they truly don’t need it).
Since I’ve spent a significant portion of my career repackaging applications, I’m all-too familiar with lazy vendors who assume users have admin rights and won’t support packaging the app to a locked-down environment, even though that’s been the enterprise standard for a decade or more (MSI was released in ’99/2000, and apps were brute-force repackaged before then).
Still, I’m not seeing a benefit to UAC in the real world. Yes, it does expose improperly-engineered apps, but that exposure doesn’t help the end user in the moment who has to deal with that poorly-engineered app…it merely exposes it and makes working with it require extra clicks on screens that a typical end-user won’t even read, or they’ll just get used to having those extra clicks. While enterprise environments will simply open specific registry perms to allow the app to work (as they already have to do), the SOHO environments will give the user admin rights-it’s faster and they don’t have the luxury of time for discovering which perms it requires.
UAC is an interesting idea, and it’s good MS put effort into solving the underlying issue: too many things in windows require admin priveleges, and too many users aren’t very savvy. Unfortunately, it seems to only address a small class of users. Hell, I don’t run any of my machines (or my family’s) machines as restricted users-the administrative overhead is just too high. It’s easier to let everyone run as admin, use good prevention and scanning tools, and clean up the machines occasionally.